PullApps 
How to use with Azure Active Directory
PullApps and Azure Active Directory
You can setup PullApps to use Azure Active Directory to define application assignments. AAD Premium is not required for this feature.
Note: Currently AAD may only be used with PullApps configured in Self-Service mode.
Setting up to use AAD requires the administrator of your AAD tenant to perform certain actions. This includes authorizing the PullApps application and setting up User Groups.
Authorizing PullApps in your Tenant
Your tenant admin will need to create an Enterprise Application record for PullApps. While the name used for this app in the tenant configuration is not actually important, we would suggest calling it PullApps. The app configuration in the tenant will define a set of permissions and create a "Secret Key" that may be used by an external application to access the tenant. This Secret Key is generated when the app configuration is performed and is not displayed after, so the administrator creating the app configuration will need to record it and provide this key for you when installing PullApps. If this key is lost, it will be necessary to create another application configuration record in the tenant.
The screen shots below show the typical configuration of PullApps in the tenant.
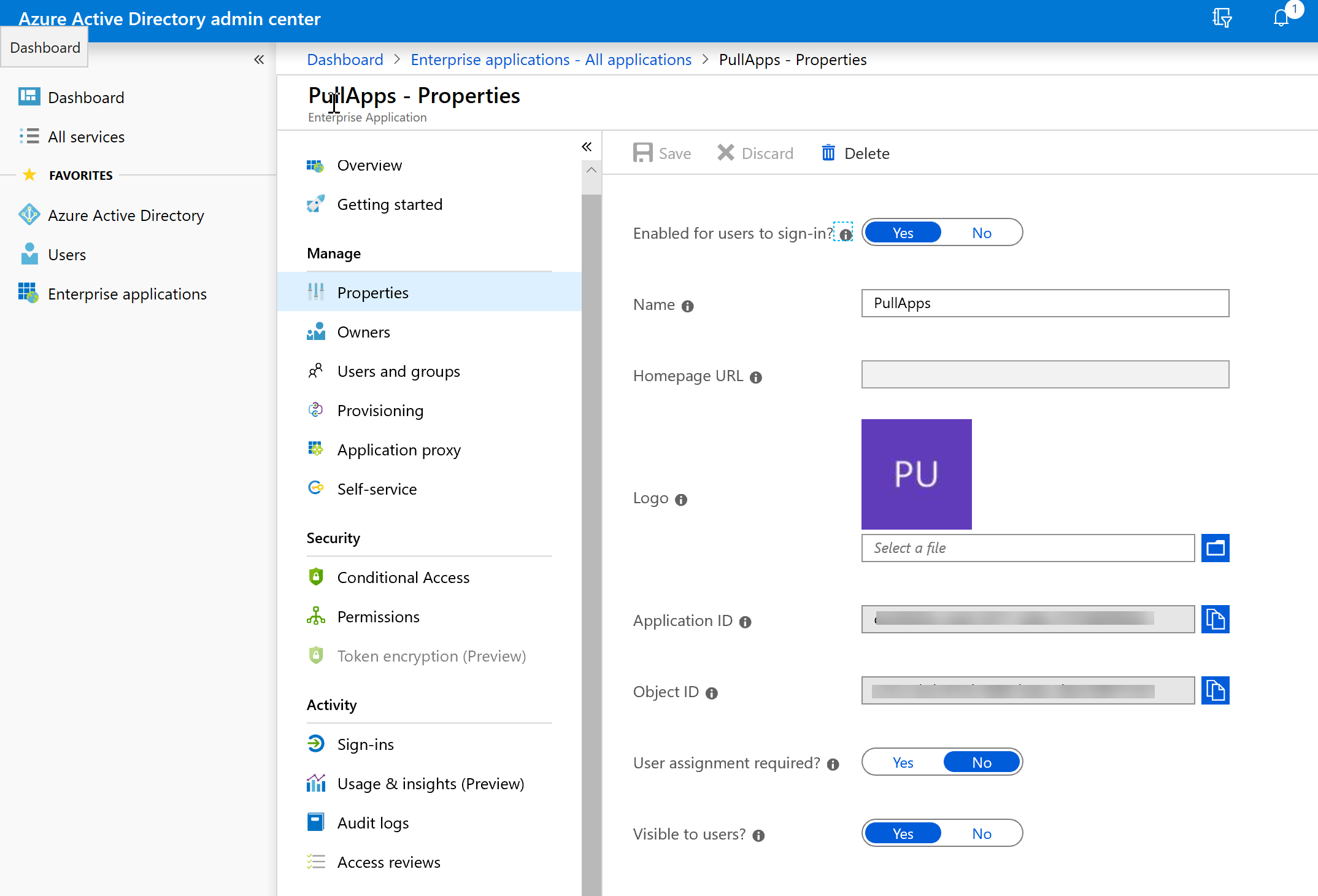
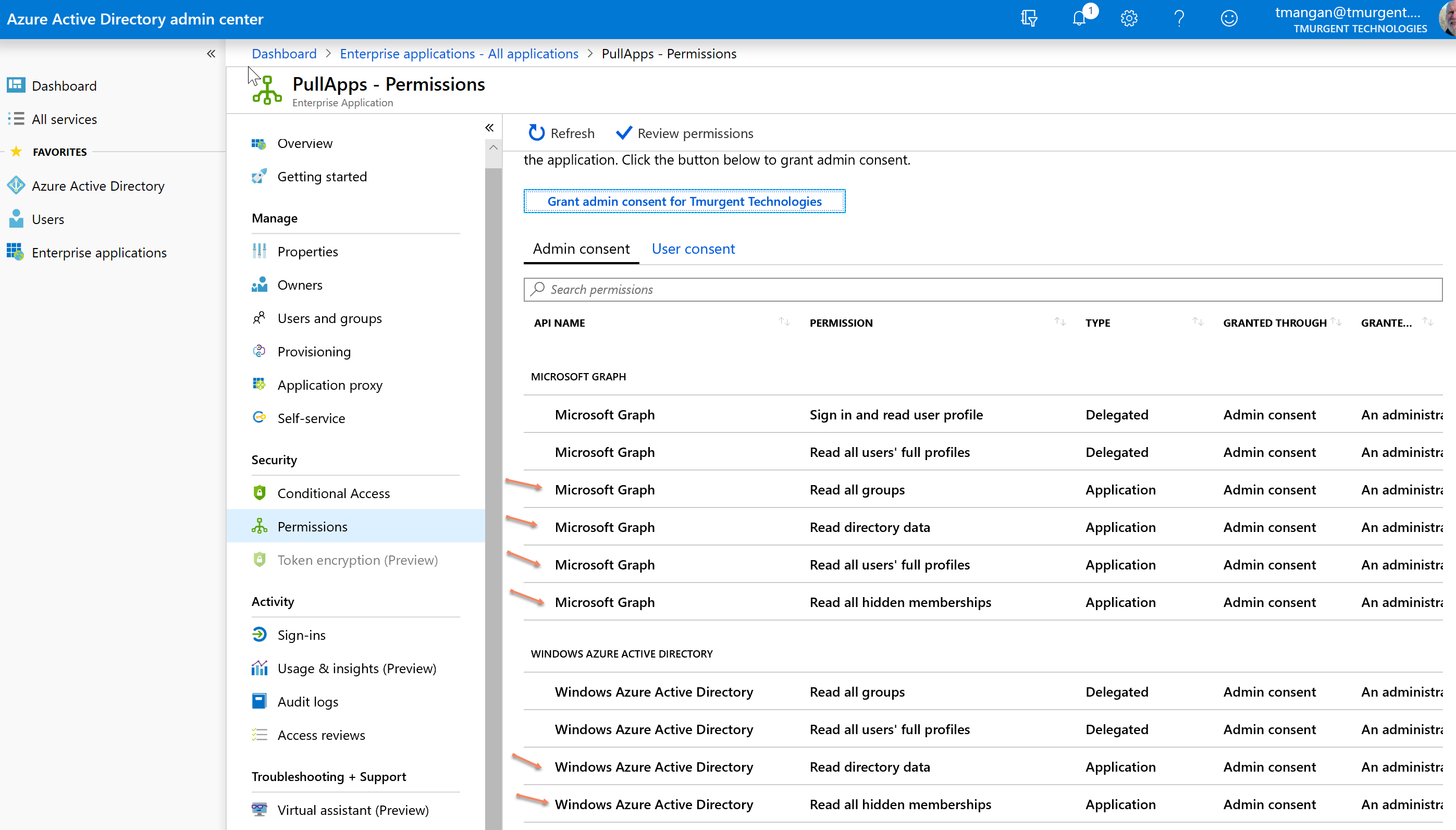
Note: After setting the permissions, there is an additional step in the tenant to authorize the requested permissions.
Creating User (Application) Groups in your Tenant
Applications are authorized by creating "User Groups" in the tenant. The name of the group should match that of the application package (Package Name field for App-V packages, Package FamilyName for MSIX packages). AAD Users are added to the group. The user simple needs to logged into windows with an associated AAD account. An example of one such group is shown here: